
This question comes up time and time again in conversations with customers who are considering moving their IT infrastructure to the cloud. For many companies, the cloud sounds like a promise – flexibility, scalability, no need to invest in expensive hardware, and the ability to launch services almost immediately. On the other hand, there are concerns, often related to loss of control over data, the risk of data leaks, or non-compliance with applicable regulations.
Are these concerns justified? For comparison, in the traditional local model, the company is responsible for purchasing equipment, configuring it, physically securing the server room, and ongoing maintenance. In the cloud, some of these responsibilities are taken over by the provider, which can be both an advantage and a source of misunderstanding. Let’s take a closer look at the mechanisms that make the cloud secure – or not – using Amazon Web Services (AWS) as an example.
Cloud security is not a one-time activity, but a process based on a clearly defined division of responsibilities between the service provider and the customer. AWS promotes the concept of a Shared Responsibility Model, which assumes a clear division of roles: AWS is responsible for the physical security of the infrastructure, network and virtualisation layer, while the customer must ensure the proper configuration of instances, operating system updates, data security and user access management. This is a key reference point for anyone considering implementing cloud solutions.
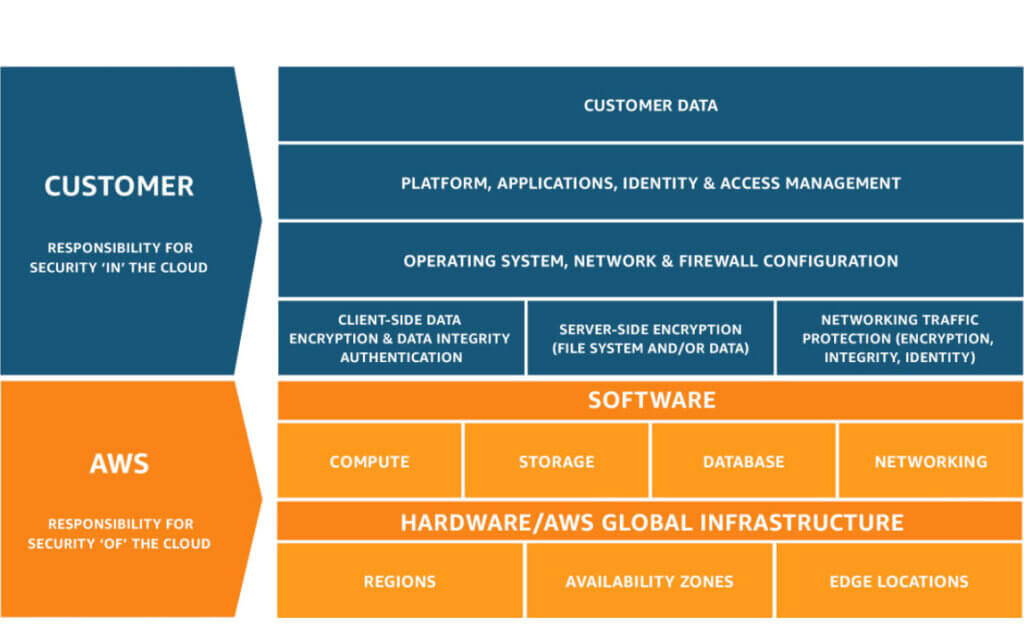
Under this model, AWS takes responsibility for the security of the infrastructure, which includes physical data centres, server hardware, network infrastructure and hypervisor, i.e. the layer that manages virtual machines. Everything above this layer – operating systems, applications, data, user accounts and how they are secured – is the responsibility of the customer.
| Area | AWS cloud | Client |
|---|---|---|
| Physical infrastructure | Yes – hardware, network, data centres | No |
| Cloud security | Yes – physical and network security | Yes – access configuration (IAM, firewalls) |
| System and data management | No – operating systems, data, backups | Yes – updates, encryption, copies |
| Applications and configurations | No | Yes – applications, AWS service configuration |
| GDPR/standard compliance | Responsible for AWS infrastructure compliance | The customer must ensure the compliance of their data processing |
This means that customers cannot assume that because data is ‘in the cloud,’ it is automatically secure. It is the customer who decides who has access to the environment, what the passwords are, whether updates are installed on time, and whether the servers are properly configured. In practice, many users are unaware of this responsibility. That is why more and more companies are choosing to work with technology partners, especially after experiences that have shown how easy it is to make a costly mistake.
For example, one company that implemented an AWS environment on its own did not notice for several months that one of its instances was open to the public. It was only an audit conducted by an external partner that revealed the vulnerability, which could have been easily exploited. The professionals not only helped to patch it, but also implemented access policies that had not been considered before. who specialise in cloud environment administration. Professional care means not only efficient implementation and configuration, but also continuous security monitoring, ongoing updates, incident response, and adapting the environment to changing threats and business needs.
Many organisations also ask whether storing data in the public cloud is compliant with the European GDPR regulation. This is an important issue, especially for companies that process personal data of customers or employees. The answer is yes, the cloud can be GDPR-compliant, but only if it is managed properly. It is crucial to choose the right data storage region – preferably within the European Economic Area – and to ensure that every data processing operation has a legal basis.
AWS offers a wide range of tools to support compliance with the GDPR, as well as other industry and international regulations such as HIPAA, PCI DSS and ISO 27001 – including encryption of data at rest and in transit, detailed access logging, identity management, and ready-made reports and audit mechanisms. However, it is the customer who acts as the data controller within the meaning of the GDPR – they determine the purposes and means of processing. Therefore, it is necessary not only to be familiar with the tools, but also to configure the environment and security policies appropriately.
One of the pillars of cloud security that is often overlooked or treated as secondary is backup. However, a well-designed backup system is often the last line of defence against data loss, whether it results from a malware attack, user error or technical failure. AWS offers a variety of solutions for creating and storing backups. We can use EBS snapshot copies, file versioning in S3, automated backup policies in AWS Backup, and data storage in different regions or availability zones. The ability to set backup schedules, define retention policies, and encryption are features that can significantly increase security.
Regular testing of backups is equally important. Many administrators only realise how useless they are when they cannot be restored. That is why one of our standard procedures for customers is to test data recovery in an isolated environment, which allows us to verify the effectiveness of the entire backup mechanism and prepare for a real emergency scenario.
So, is the cloud secure? Yes, provided that we know how to use it. The cloud is a tool, not a magic solution that eliminates all threats – just like a car, which does not guarantee safe driving on its own. Only in the hands of a trained driver, with the right knowledge and regular servicing, does it become a safe means of transport. Similarly, the cloud requires conscious use and proper management. Designed with care, monitored on an ongoing basis and developed together with the organisation, it can be much safer than many traditional local solutions. But – and this is important – it requires knowledge, attention and responsibility.
Just as we do not run a business without an accountant, we should not manage the cloud without proper technical support. That is why a well-chosen technology partner is not a cost – it is an investment in security and peace of mind.